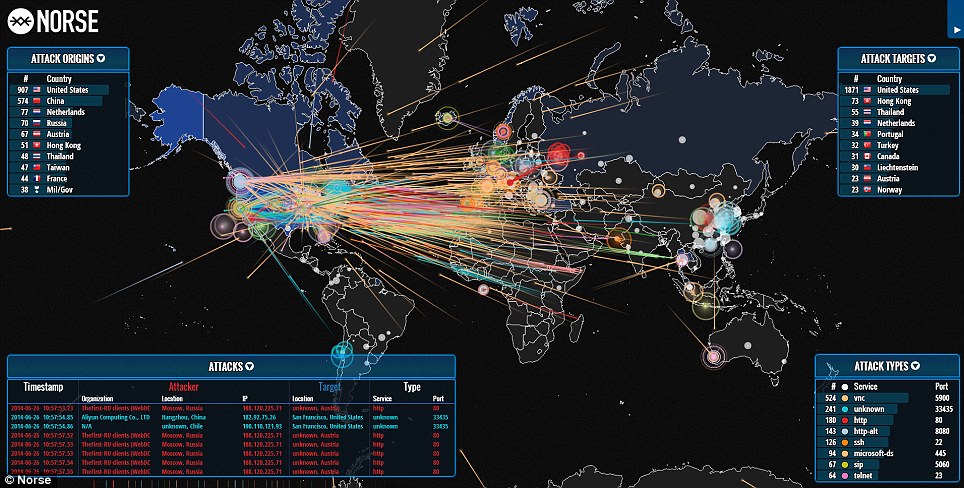
This is the final part of the Paper. In this part the authors explains the reasons why Cyber War will not take place.
Non- state actors could also carry out cyber attacks that aim to control or disrupt system whether for ideological or criminal reasons. However, such groups do not have the same abilities as large states. As cyber attacks on a high- valued targets such as defense systems or military objects require both high level of knowledge of cyber space but also deep understanding of hacking highly encrypted codes.
Non- state actors could also carry out cyber attacks that aim to control or disrupt system whether for ideological or criminal reasons. However, such groups do not have the same abilities as large states.
Radicalization in Cyber Space 
And nowadays there is a rising threat of radicalization in cyber space as the growing usage of advanced technologies and computer skills not only among individuals and soldiers, but also including terrorist groups, creates the possibility for a cyber war with a special focus on civilian target such as airports, power stations, and military command structures (Gray 2007). Although the fact those radical groups do not have such capabilities in cyber war at the present time, there is a strong possibility that sooner or later they would achieve cyber superiority.
Furthermore, the information systems generate vulnerabilities for large and rich states due to the fact that it enhances profitability and easily disorders targets for terrorist groups. And it is almost impossible to make a modern IT system without some vulnerabilities waiting to be exposed. Therefore the growing concern of the importance of cyber security has impact on cyber space, and more significantly on the real life situations. However, “cyber attacks appear much less useful than physical attacks: they do not fill potential victims with terror, they are not photogenic, and they are not perceived by most people as highly emotional events” (Lachow 2009, p. 450). As a consequence, terrorist groups are not considering the cyber attacks as potential future events.
Cyber War and Clausewitz
On the other hand, with reference to Thomas Rid’s article ‘Cyber war will not take place’ (2011) the existence of an opinion that there is no cyber war in the past, in the present or future due to many facts. Initially, there is no clear explanation and no legal entity for what does ‘cyber war’ mean and how it should be understood. Therefore, the question arises, is there an actual existence of cyber war in the real world? According to Carl von Clausewitz (1832, 1980), there are three elements of war. The first component of war is violent character; the real war is always assumed as the act of physical violence and deaths of innocent citizens.
It should be mentioned that the actions of cyber attacks are usually anonymous and in general are hard to identify and detect. As a result, there is no clear evidence of the beginning of war or attack in the cyber space
Therefore, if there is no an actual act of violence, there is no war. Furthermore, the concept of cyber war is not providing a clear explanation what are the weapons of it, and how to respond to these arms. Which resulted in the non- existence of cyber war itself in the legal framework, “the only issue that has been defined by international agreement is a nation’s right to self defense when attacked, and that applies only to the traditional manner of attack, i.e., ‘armed’ attack” (Carr 2010, p. 39). The second element of Clausewitz explanation of war is instrumental character, he stated that the act of war is instrumental; it has a means and an end (Rid 2011). The actions of violence and threat are the means, and to reach the end of the war the opponent has to be a defenseless and accept the offender’s will (Clausewitz 1832, 1980).

It should be mentioned that the actions of cyber attacks are usually anonymous and in general are hard to identify and detect. As a result, there is no clear evidence of the beginning of war or attack in the cyber space, and no clear distinction of the offender and his will. The third element of Clausewitz meaning of war is its political nature, where in the real world the act of war is supposed to have a political purpose and use of force. Furthermore, in order to “be political, a political entity or a representative of a political entity, whatever its constitutional form, has to have an intention, a will” (Rid 2011, p. 8). To put it in another way, the “Cyber Warfare is the art of science of fighting without fighting; of defeating an opponent without spilling their blood” (Carr 2010).
Geography of Cyber Space
The cyber space is ideal fighting ground as the geography of cyber space is much more mutable than any other environment. For instance, as Gregory Rattray said mountains and oceans are difficult to move, whether the extents of cyber space could be turned on and off with the click of a switch (2009). What it basically means in international affair that in critical moments there is a possibility for a limitation of government’s ability to communicate internationally and control what is going to be heard in the global arena. As a matter of fact that is what happened in Georgia in 2008.
There was a cyber attack organized by Russian government against Georgian websites with a simultaneous military operations happening in South Ossetia
There was a cyber attack organized by Russian government against Georgian websites with a simultaneous military operations happening in South Ossetia (Nazario 2008). The cyber attack on Georgia covered three different types. The first on is attack on country’s website were defaced, for example Georgia’s national bank and the ministry of foreign affairs, one of the most notable defacement was a collage of portraits juxtaposing Adolf Hitler and Mikheil Saakashvili, the Georgian president (Rid 2011). The second type of cyber attack was on Georgian public and private sectors, including state websites, like the parliament, but also news media, the Georgian’s largest commercial bank, and others insignificant websites. And the third approach was on distribution of malicious software that intensified the degree of attack (Rid 2011). It should be mentioned that it was the first time in history on cyber space where there was a simultaneous military actions and cyber attacks.
Conclusion : A New Battlefield
In conclusion, it should be mentioned that at the present time the world is changing to the highly charged battlefield of the ideas. This is not the world where material resources are valued as the main subject of embittered competition between power states. It is the new emerging world where the strategic planning and management of the information capabilities and cyber resources is the key elements to the success in the global arena. The information resource became an important element in the world; the humankind has reached this stage of development where the regular laptop in the hands of professionals could become a weapon.
Furthermore, nowadays the world is depending on computers as many things are controlled by it: the pressure in the pipelines, the operation of the power systems, and the movement of aircrafts, hospitals and emergency services. These systems are operating under special software and therefore are vulnerable for viruses that could lead to phenomenal effects with the infliction of economic and physical damage comparable to the impact of conventional arms. This essay includes two main viewpoints of cyber war, the first one is supported by Jeffrey Carr, Singer and Friedman, and Rattray, who argued in favor of the existence of cyber war and second one is Thomas Rid who stated that there is no cyber war and it will not take place in the future. According to Thomas Rid there is no clear evidence that cyber war exist, only subversion, espionage and sabotage (2011). He argues that at the present time there is no known act of cyber war where clear explanation of war is defined.
And the political cyber offences, whether they are criminal or not, should not be defined as neither common crime nor common war. Therefore, nowadays there is no confirmation of cyber war that is going on in the global arena. On the other hand, the continuous cyber attacks and the circulation of the idea of possible cyber war are discomposing more and more individuals, military and state minds around the world. The CSIS, the Center of Strategic and International Studies, established many research papers about probability of cyber war and the importance of cyber security nowadays, they also declared that cyber warfare should be concerned as serious as a missile threat.
It should be mentioned that cyber war is the cheapest and effective way of disabling the civil and defensive facilities. Furthermore, the most technological advanced countries are the most vulnerable for the cyber attacks, as currently states, public organizations, and private companies are transferring their management activities to the Internet or a public data networks. To conclude, although there is no clear explanation of cyber war and legal framework of how governments are allowed to react to this kind of attack, and the fact that cyber war is not violent, there is still evidence of the continuous cyber war between states, like Georgia and Russia in 2008, and therefore there is an existence of cyber war in the real world.
Bibliography:
Carr, J. (2010) Inside Cyber Warfare. Sebastopol, O’Reilly Media, Inc.
Clausewitz, C. (1832, 1980) Vom Kriege. Berlin: Ullstein.
CSIS commission (2008) Securing cyberspace for the 44th presidency: a report of the CSIS commission on cyber security for the 44th Presidency. [pdf] Washington: Center for Strategic and International Studies. Available at: http://csis.org/files/media/csis/pubs/081208_securingcyberspace_44.pdf. [Accessed 1 December 2014].
Dunlap, C.J. (1998) The Law of Cyber war: a case study from the future. In Campen A.D. & Dearth D.H. (Eds) Cyber war 2.0: Myth, Mysteries and Reality. Fairfax, AFCEA International Press.
Gray, J. (2007) Al Qaeda and what it means to be modern. London, Faber and Faber Limited.
Lachow, I. (2009) Cyber terrorism: menace or myth. In Kramer F.D. & Starr S.H. & Wentz L.K. (Eds) Cyber power and National Security. Washington, Potomac Books, Inc.
Lewis, J. (2003) Interview in: Frontline: Cyber war. PBS. Available at: http://www.pbs.org/wgbh/pages/frontline/shows/cyberwar/interviews/lewis.html. [Accessed 1 December 2014].
Nazario, J. (2008) Georgia DDoS Attacks – A Quick
Summary of Observations. Available at: http://www.arbornetworks.com/asert/2008/08/georgia-ddos-attacks-a-quick-summary-of-observations/. [Accessed 1 December 2014]
Petersen, J.L. (1998) Living in a Wired World: Cyber Society 2020. In Campen A.D. & Dearth D.H. (Eds) Cyber war 2.0: Myth, Mysteries and Reality. Fairfax, AFCEA International Press.
Rattray, G.J. (2001) Strategic Warfare in cyberspace. Cambridge, Best-set Typesetter Ltd.
Rattray, G.J. (2009) An Environmental Approach to Understanding Cyber power. In Kramer F.D. & Starr S.H. & Wentz L.K. (Eds) Cyber power and National Security. Washington, Potomac Books, Inc.
Rid, T. (2011) Cyber War Will Not Take Place. Journal of Strategic Studies, 35:1, 5-32.
Singer, P.W. & A. Friedman (2014) Cyber security and Cyberwar: what everyone needs to know. New York, Oxford University Press.